Examining network interactions through Packet Capture and Analysis proves invaluable in identifying both inefficient transmissions and potential cybersecurity threats.
Packet Capture involves intercepting and gathering data packets as they traverse a network connection. These recorded packets are then scrutinized to pinpoint and address network issues such as high latency and disruptions. The insights gained from packet analysis serve as a valuable resource for Network Administrators, enabling them to efficiently troubleshoot and rectify network faults.
Packet Analysis is instrumental in various tasks, including:
- Identifying security vulnerabilities
- Resolving DNS issues
- Addressing and resolving network connectivity issues
- Detecting and addressing network problems
- Identifying and rectifying packet leaks
- Detecting and preventing malware
Whether capturing complete data packets or specific segments, a full data packet comprises two essential parts: a payload and a header. The payload contains the actual contents of the packet, while the header provides crucial information such as the packet’s source and destination addresses.
In the realm of Full Packet Capture and Analysis, we’ve compiled a list of applications to facilitate these processes.
Colasoft Capsa
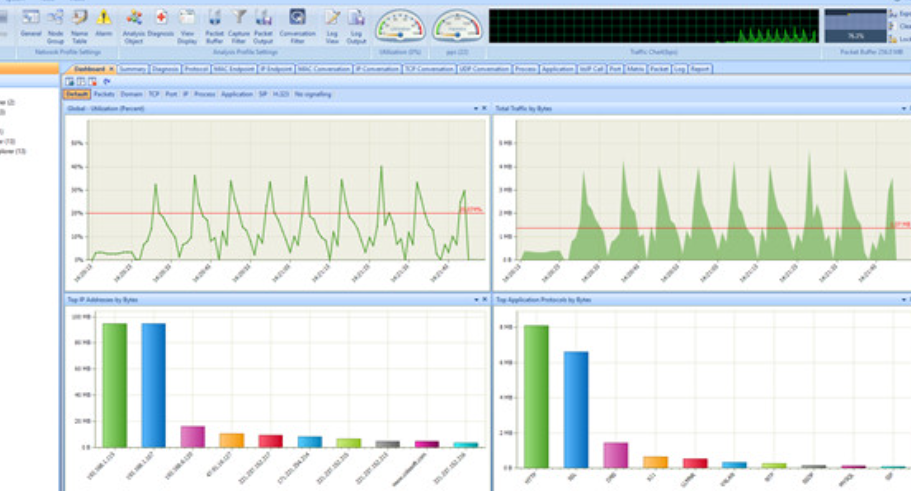
Capsa serves as a real-time, portable network analyzer, tracking, and diagnostics tool applicable to both wired and wireless networks. You can schedule Information Packet examinations to run at specified intervals, such as regularly or monthly. Regular scans ensure that you stay vigilant to any performance issues that may arise. In case you overlook anything, email and audio alerts will promptly notify you whenever a networking session requires your attention.
Capsa is designed to keep users informed about vulnerabilities and potential threats that could result in service disruptions. This tool adeptly monitors crucial VoIP (Voice over Internet Protocol) metrics, including call codec type and event flow. It proves to be an outstanding resource for individuals keen on engaging in packet examination, providing a valuable learning experience for identifying network issues and enhancing network security.
Functions:
- Free integrated energies for developing and replaying packages, in addition to scanning and pinging IP addresses.
- Medical diagnoses network problems and advise services instantly.
- Supports VoIP and TCP circulation analysis, which can be utilized to identify network concerns such as sluggish reaction time and CRM (Customer Relationship Management) deals.
- DDoS attack, ARP attack, and TCP port scanning can be discovered, and it likewise enables the user to identify the technical problems in the network.
- This tool supports over 1800 procedures, making it easy to take a look at procedures in a network and understand what’s going on.
- It gathers all information packages and reveals complete package sequencing details in Hex, and ASCII format. (In-depth package decoding)
- Network traffic and throughput info can be shown in charts formats.
Colasoft offers other tools such as Network Performance Analysis System (nChronos) and Unified Performance Management Solution (Colasoft UPM). It supplies a 30-day totally free trial to examine the functions prior to purchasing.
TCPDump
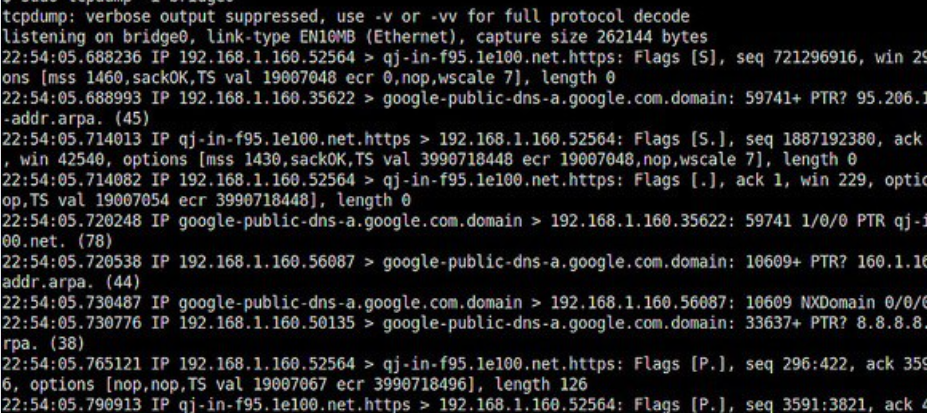
TCPDump stands as an open-source and potent command-line packet analyzer tool adept at capturing processes like TCP, UDP, and ICMP (Internet Control Message Protocol). This tool is pre-installed on all Unix-like operating systems and operates under the BSD license. Easily examining the headers of TCP/IP packets, TCPDump swiftly provides information for each data transmission, running the script until you terminate it using the Ctrl+C option.
Setting up Tcpdump is straightforward, and once you grasp the tool’s usage, flags, and arguments, it becomes a valuable resource for troubleshooting connection issues and enhancing network security. Recorded data packets are stored in a file for further analysis using tcpdump. The tool saves the file in PCAP extension format, easily reviewable with tcpdump or Wireshark, which reads PCAP (short for packet capture) format files.
Functions:
- Filtering the caught information packages by source, location, and procedure is possible.
- Free and open-source
Paessler PRTG
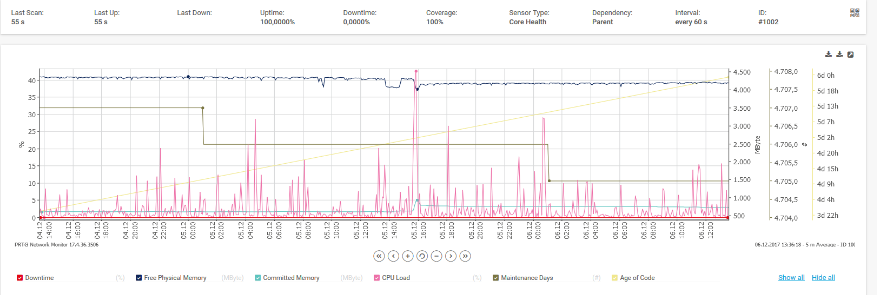
Paessler PRTG Network Monitor stands out as one of the widely used tools for network monitoring and traffic analysis, providing crucial insights into your network’s infrastructure and performance.
Compatible with Windows, this tool encompasses a variety of monitoring options, including bandwidth tracking and traffic analysis. Paessler PRTG offers a free version, utilizing a combination of a packet sniffer, WMI, and SNMP to report network performance metrics.
Functions:
- Flexible notifying— PRTG has more than 10 created innovations, consisting of SMS, push notices, e-mails, setting off HTTP demands, and so on.
- Numerous User Interfaces— constructed on AJAX with strong security requirements, extremely performant attributable to Single Page Application (SPA) innovation,
- Cluster failover option— To make up a somewhat raised tracking option.
- Maps and control panels— Use real-time maps including existing live details to imagine the network.
- Dispersed tracking— Using Portable Interceptors, you can keep an eye on various networks in numerous areas and numerous networks within your company.
Comprehensive reporting presented through numbers, data, and charts is a hallmark of this tool.
Supporting various alert methods, including SMS, emails, and third-party integrations with platforms like Slack, PRTG is available in an unlimited version for a 30-day trial. Following the free period, it reverts to the free version.
Wireshark

Wireshark is a free and open-source packet analyzer that empowers you to examine real-time network data transmissions. This tool enables network administrators to delve into the network at a granular level to identify the origins of traffic issues and errors. It is an excellent tool that necessitates a solid understanding of networking principles.
Functions:
- It almost deals with any os, consisting of Windows, Linux circulations, Mac OS X, and so on.
- Produce reports based upon existing analytical information.
- Filtering the output can be made with a range of alternatives, such as timers and filters.
- Picture network packages with IO charts and charts.
- It can likewise tape-record USB traffic.
- It provides a large range of usages, consisting of fingerprinting unapproved traffic, package filtering settings, and so on.
- Color-coding guidelines can be used to recognize the kinds of traffic.
- In-depth VoIP (Voice over Internet Protocol) research study.
Lost information packages, network latency issues, Application dependences, and Inefficient window sizes are the typical troubleshooting difficulties that Wireshark might aid with. This tool permits you to keep track of network traffic and supplies systems for browsing and identifying the source of a concern.
Unicast (connectionless) traffic that isn’t sent out to the network’s MAC address user interface can likewise be kept track of with the Wireshark tool.
Arkime

Arkime operates collaboratively with the existing security system to collect and index network traffic and data transmissions in a standard PCAP format.
All recorded data packets are stored and exported in the common PCAP format, allowing you to utilize your preferred PCAP ingesting tools, such as Wireshark or tcpdump, in your analytic process.
PCAP retention is determined by the amount of sensor disk space available, while API retention is influenced by the size of the Elasticsearch cluster. Both of these parameters can be adjusted at any time.
Designed to function across various platforms and scales, Arkime can handle tens of gigabits per second of traffic. All PCAP format files generated by Arkime sensors can be configured and accessed solely through the Arkime web interface or API. Additionally, PCAP files can be encrypted at rest with Arkime.
Functions:
- Provides an easy to use web user interface for taking a look at, finding, and drawing out PCAP files.
- Free and open source
- Permits other PCAP ingesting tools to examine the conserved PCAP files.
Conclusion
Interpreting packet capture data typically demands a considerable level of technical expertise, a proficiency attainable through the utilization of these tools.
I hope you found this article exceptionally valuable in exploring Full Packet Capture and Analysis tools suitable for networks of various sizes, from small to large.

